Explosive adoption, limited trust.
MCP is not encountering resistance despite its success.
It is encountering resistance precisely because of its success.
When a technology really works, it stops being treated like a demo.
And it starts to be judged on the only thing that matters: control.
That's what's happening with MCP – Model Context Protocol.
In just over a year, it has become the common language with which artificial intelligence models communicate with tools, data and systems. It is everywhere: in developer tools, prototypes and experimentation workflows.
Yet, just as adoption is accelerating, companies are doing the opposite of what one would expect:
they are not exposing it.
They are closing it off.
They mediate it behind increasingly rigorous layers of control.
Contradiction?
Only if you look at MCP through the wrong lens.
A year of MCP, looking at the facts
In November 2024, Anthropic presented the Model Context Protocol, describing it as “the USB-C of AI”: an open standard for connecting models and tools without custom integrations.
In March 2025, OpenAI officially adopts it.
Google follows shortly after.
By the end of 2025, MCP SDKs exceed 97 million monthly downloads.
Then comes the signal that really matters.
In January 2026:
Microsoft disables MCP by default in enterprise environments
GitHub Copilot requires centrally approved authorisation lists
Salesforce keeps MCP only in pilot mode, with continuous monitoring
The most widely used protocol in modern AI is also the one that companies least want to leave exposed in production.
This is not a warning sign.
It is typical behaviour for an organisation when a technology ceases to be experimental and starts to really matter.
It's not an accident
It's a rational and predictable reaction to a technology that has stopped being optional.
The level that really makes the difference
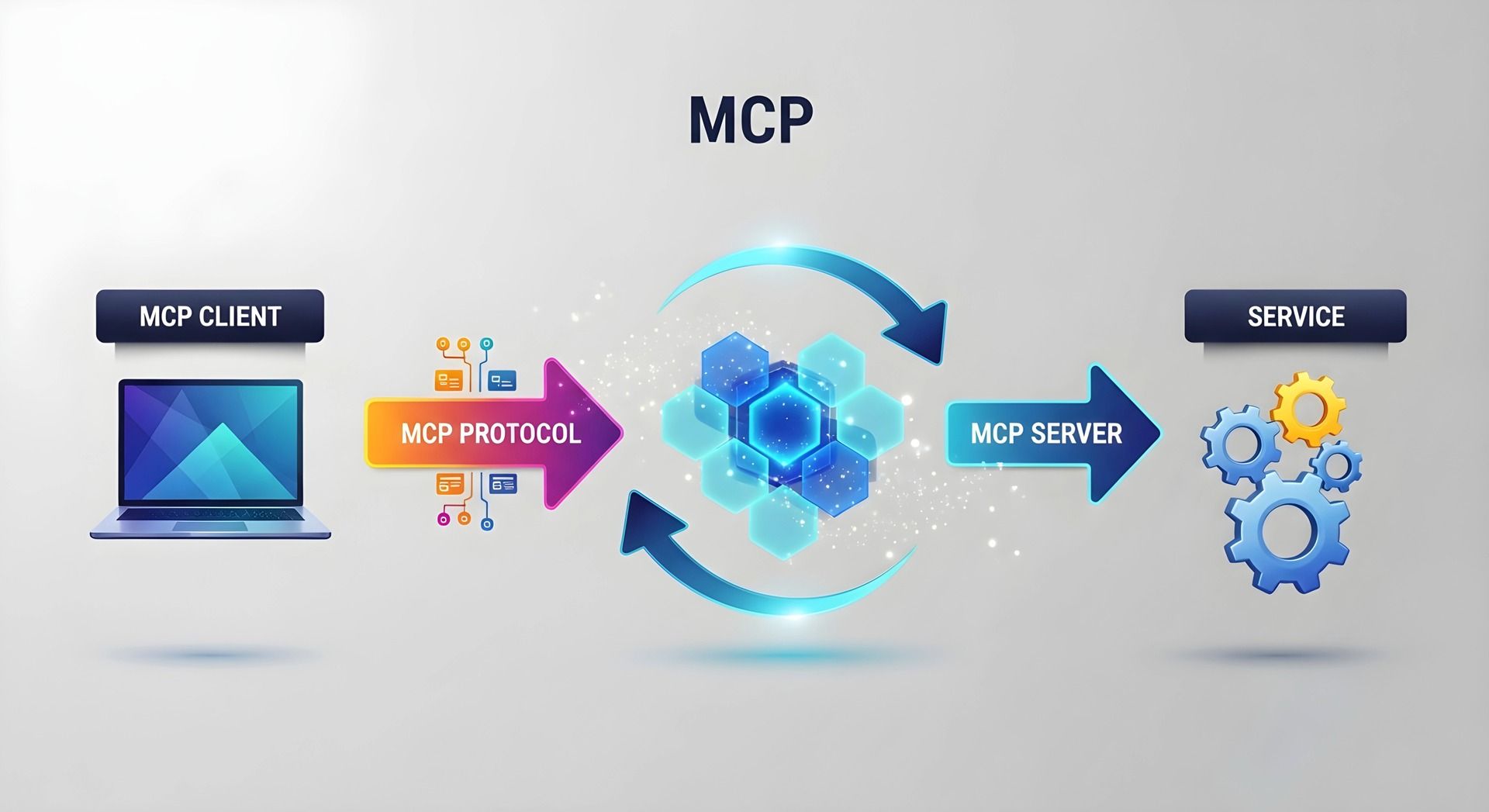
MCP (Model Context Protocol) is a protocol that enables artificial intelligence models to connect to external tools, data, and services in a standardised manner.
In practice, it defines how the model can “ask” the system to do something — read a file, query a database, call an API — without custom integrations.
That's what makes it so powerful: once adopted, tools become immediately accessible to AI agents.
And that's also why companies have started treating it with extreme caution.
What big companies really do with MCP
(spoiler: not what you think)
The adoption numbers are impressive.
The way MCP is released into production is much more cautious.
Bloomberg: speed yes, exposure no
Bloomberg has stated that it has reduced time to production ‘from days to minutes’ thanks to MCP.
But not by exposing MCP.
It has built an internal mediation layer that translates, validates and controls every call.
The result is a system in which agents and tools collaborate freely, but under total control.
Amazon: MCP as an adapter, not as a surface
Amazon says (quoted by The Pragmatic Engineer) that ‘most internal tools have added MCP support’.
The key detail is another: Amazon has been API-first for over 20 years.
MCP does not replace APIs.
It translates them.
Security was not added later.
It was already part of the infrastructure.
Microsoft: the most honest signal
GitHub Copilot Business and Enterprise make MCP:
disabled by default
only activatable with explicit rules
governed by organisational allowlists
In an official discussion on GitHub, one comment summarises the position:
“MCP servers are too dangerous to be released at an organisational level without strict controls.”
The pattern is always the same:
MCP lives inside. It is never directly exposed.
The data that explains why
Here, the picture becomes less emotional and clearer.
A 2025 academic study analysed 1,899 open source MCP servers:
7.2% with generic security vulnerabilities
5.5% vulnerable to MCP-specific tool poisoning
66% with code defects👉 https://arxiv.org/abs/2506.13538
A second study showed that an LLM can be induced, via MCP, to:
execute malicious code
steal credentials
gain remote control over connected systems👉 https://arxiv.org/abs/2504.03767
Independent scans (Knostic, Backslash Security) then found thousands of MCP servers:
without authentication
with excessive permissions
exposed on internal and public networks
The data that matters for decision-makers:
only 28% of Fortune 500 companies have MCP in production
75% use it behind gateways, audits and data loss prevention rules
Gartner puts it diplomatically:
By 2026, 75% of API gateway providers will include MCP features.
👉 https://www.gartner.com/en/articles/api-gateway-trends
Meaning: the control infrastructure is arriving now.
The truth that the industry is now realising
MCP is not an application standard like HTTP or OAuth.
It is an infrastructure layer.
The problem is not that MCP is immature.
The problem is that it has been judged as if it should be exposed, when in fact it was created to be mediated.
It is a classic category error.
Three realistic ways in which MCP is used today
1. MCP as a secure “operations centre”
In enterprises, MCP lives behind:
API Gateway
firewalls and IP filters
automatic rules on sensitive data
mandatory logging of every call
Microsoft Copilot Studio makes it explicit: MCP is only accessible through governed connectors
2. MCP as a “personal lab”
The 97 million downloads are not corporate releases.
They are developers using MCP locally, on Claude Desktop, Cursor, VS Code.
It is secure precisely because it does not touch production.
This explains the paradox:
very fast on laptops, very slow in data centres.
3. MCP “dual track” (the near future)
Open prototypes for experimentation.
Secure production for release.
Private registries, centralised governance, clear separation of layers.
This is the model that is emerging for 2026.
Why at ELECTE we treat MCP as infrastructure, not magic
At ELECTE, we work with European SMEs that want to use AI without turning it into an operational risk.
That's why MCP is not a feature to be sold.
It is a layer to be governed.
When we integrate data and tools:
MCP lives in the backend
behind controlled APIs
with limited scopes and complete tracking
The customer sees analysis, not protocols.
This is not excessive caution.
It is the lesson that emerges from observing what Bloomberg and Amazon do, not what demos promise.
Three concrete steps (not “wait and see”)
1. Experiment now, but within the right perimeter
Use MCP locally to understand its potential, without risk.
2. Build governance before integrating
Tool registry, logging, sensitive data blocking.
Without this, MCP does not go into production.
3. If you build AI products, always separate the layers
Internal MCP for speed.
External API for control.
The verdict
MCP is not immature.
It is a technology that arrived before the infrastructure that makes it governable.
The right question for 2026 is not:
"Is MCP mature?"
But:
"What layer of MCP are we ready to control?"
Because the future of enterprise AI will not be
“all open via MCP”,
but
“all controlled, via mediated MCP”.
This is not an opinion.
It is what happens when a technology becomes useful enough that it can no longer be ignored — and enters real systems.
MCP cannot be stopped.
We can only decide how it enters corporate systems, where it passes and who governs it.
And it is on these decisions — not on adoption itself — that the difference between experimentation and production is played out.
Fabio Lauria
CEO & Founder, ELECTE S.R.L.
Sources and further reading
Official MCP repository (GitHub)
MCPSafetyScanner (open source tool)
Knostic report on exposed MCP servers
Backslash Security MCP exposure report
Xenoss – MCP enterprise adoption report
Linux Foundation – MCP governance (July 2025)
Welcome to the Electe Newsletter
This newsletter explores the fascinating world of artificial intelligence, explaining how it is transforming the way we live and work. We share engaging stories and surprising discoveries about AI: from the most creative applications to new emerging tools, right up to the impact these changes have on our daily lives.
You don't need to be a tech expert: through clear language and concrete examples, we transform complex concepts into compelling stories. Whether you're interested in the latest AI discoveries, the most surprising innovations, or simply want to stay up to date on technology trends, this newsletter will guide you through the wonders of artificial intelligence.
It's like having a curious and passionate guide who takes you on a weekly journey to discover the most interesting and unexpected developments in the world of AI, told in an engaging way that is accessible to everyone.
Sign up now to access the complete newsletter archive. Join a community of curious minds and explorers of the future.
